Redd.it malware has emerged as a significant threat to internet users globally. This harmful software jeopardizes your digital security and privacy. In this detailed guide, we will examine the nature of this threat, its potential impact, and how you can safeguard your devices. If you're concerned about Redd.it malware, you've come to the right place.
As cyber threats continue to evolve, understanding Redd.it malware is essential for maintaining the integrity of your digital environment. This article aims to provide you with practical advice and actionable insights to help shield your system from potential harm.
Regardless of your technical expertise, this guide will empower you with the knowledge to recognize Redd.it malware and implement necessary precautions. Let's delve deeper into this topic and discover how to stay safe online.
Read also:Discover The Inspiring Journey Of Emily Camp
Table of Contents
- What is Redd.it Malware?
- Common Types of Redd.it Malware
- How Redd.it Malware Spreads
- Signs Your System is Infected
- Prevention Strategies Against Redd.it Malware
- The Removal Process
- Impact of Redd.it Malware on Users
- Case Studies: Real-Life Examples
- Expert Advice for Enhanced Security
- Conclusion
Understanding Redd.it Malware
Redd.it malware refers to a specific category of malicious software that targets users via the widely used social media platform Reddit. This malware often disguises itself as legitimate content, such as links or downloads, making it challenging for users to detect. Once installed, it can compromise personal data, steal sensitive information, or impair system performance.
The primary objective of Redd.it malware is to exploit vulnerabilities in users' systems, often resulting in unauthorized access or financial losses. To effectively counter this threat, it is crucial to understand its origins and mechanisms.
A Brief History of Redd.it Malware
Redd.it malware first gained attention when users reported suspicious activities linked to Reddit. Over the years, it has evolved into a sophisticated threat, employing advanced techniques to bypass security measures. This evolution underscores the importance of staying informed about the latest developments in cyber threats.
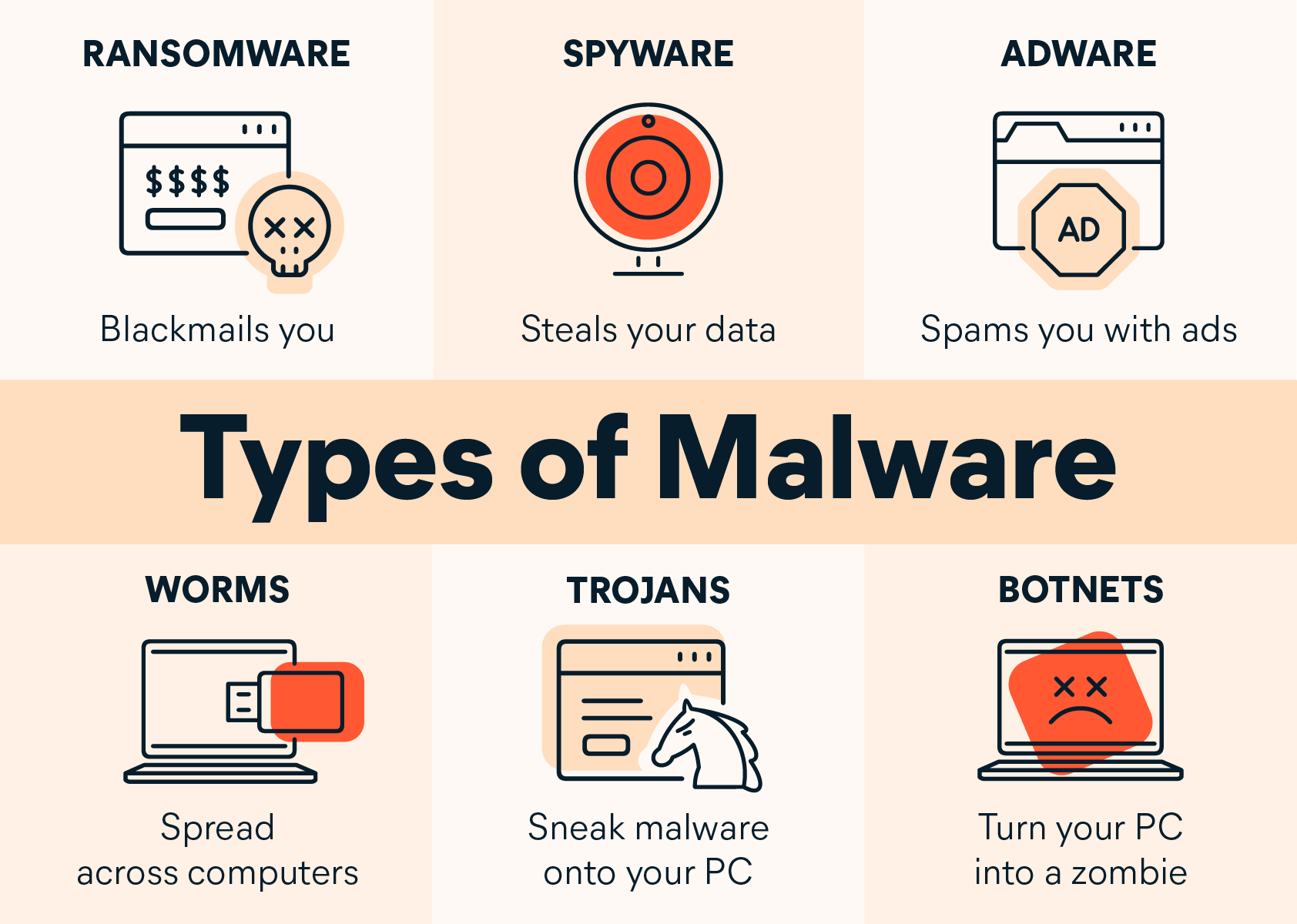
Exploring Common Types of Redd.it Malware
There are various types of Redd.it malware, each with distinct characteristics and methods of operation. Below, we provide an overview of the most prevalent forms:
- Adware: Displays intrusive advertisements and collects browsing data, often degrading user experience.
- Trojans: Conceals itself as legitimate software to infiltrate systems, allowing attackers to gain unauthorized access.
- Ransomware: Encrypts files and demands payment for decryption, causing severe financial consequences.
- Keyloggers: Records keystrokes to steal passwords and sensitive information, compromising user security.
Understanding the Distinctions
Each type of Redd.it malware poses unique risks. For instance, while adware primarily affects user experience, ransomware can lead to significant financial losses. Recognizing these distinctions is vital for implementing appropriate countermeasures and mitigating potential damage.
How Redd.it Malware Propagates
Redd.it malware spreads through multiple channels, including:
Read also:Comprehensive Guide To The Hartford Liability Insurance For Businesses
- Malicious links shared in comments or posts on Reddit.
- Phishing emails that mimic legitimate correspondence from Reddit.
- Compromised accounts used to distribute infected content.
User behavior plays a critical role in the proliferation of Redd.it malware. Engaging with unfamiliar links or downloading unverified files increases the likelihood of infection. It is essential to remain cautious and skeptical of suspicious content to minimize risks.
The Role of Social Engineering
Social engineering tactics are frequently employed to deceive users into downloading Redd.it malware. These tactics exploit human psychology, making it imperative to stay vigilant and informed. By understanding these techniques, users can better protect themselves against potential threats.
Detecting Redd.it Malware Infections
Identifying Redd.it malware early is crucial for minimizing damage. Common signs of infection include:
- Unusual pop-ups or intrusive advertisements disrupting your browsing experience.
- Sluggish system performance, which may indicate the presence of malicious software.
- Unexplained data usage or network activity, suggesting unauthorized access.
- Unexpected changes to browser settings, such as altered homepages or default search engines.
Regularly monitoring your system for these symptoms can help detect and address infections promptly, preventing further complications.
Enhancing Detection Capabilities
Utilizing robust antivirus software and conducting regular system scans can significantly improve detection capabilities. Enabling real-time protection features provides an additional layer of security, helping to identify and neutralize Redd.it malware before it causes harm.
Effective Prevention Strategies Against Redd.it Malware
Preventing Redd.it malware requires adopting proactive measures. Below are some practical strategies to enhance your system's security:
- Install reputable antivirus and anti-malware software to detect and remove threats.
- Regularly update your operating system and applications to patch vulnerabilities.
- Avoid clicking on suspicious links or downloading files from untrusted sources.
- Use strong, unique passwords for all accounts to reduce the risk of unauthorized access.
Implementing these practices can substantially reduce the likelihood of Redd.it malware compromising your system, ensuring a safer digital environment.
Importance of Education and Awareness
Staying informed about the latest cyber threats and prevention techniques is crucial for maintaining security. Regularly educating yourself and others about Redd.it malware helps foster a culture of vigilance and responsibility, reducing the overall risk of infection.
Steps for Removing Redd.it Malware
If your system becomes infected with Redd.it malware, immediate action is necessary to minimize damage. Follow these steps for effective removal:
- Disconnect from the internet to prevent further data transmission and protect sensitive information.
- Boot your computer in safe mode to limit malware activity and facilitate removal processes.
- Run a comprehensive system scan using trusted antivirus software to identify and neutralize threats.
- Remove any detected threats and reset affected settings to restore your system's functionality.
In complex cases, seeking professional assistance ensures thorough removal and restoration of your system, providing peace of mind and long-term security.
Post-Removal Best Practices
After successfully removing Redd.it malware, take additional steps to secure your system and prevent future infections. Update all software to patch vulnerabilities, change passwords for enhanced protection, and monitor your system for any lingering issues. These measures contribute to a more secure digital environment.
The Impact of Redd.it Malware on Users
The consequences of Redd.it malware can be severe, affecting both individuals and organizations. Potential impacts include:
- Data breaches leading to identity theft and financial fraud.
- Financial losses resulting from unauthorized transactions or ransomware demands.
- Reputational damage caused by compromised accounts and compromised trust.
Recognizing these impacts emphasizes the importance of adopting proactive cybersecurity measures to safeguard personal and organizational data.
Legal and Ethical Implications
Redd.it malware not only affects users but also raises significant legal and ethical concerns. Developers and distributors of such malware may face severe legal consequences, underscoring the need for responsible digital behavior. By promoting awareness and accountability, we can work towards a safer online community.
Real-Life Case Studies of Redd.it Malware
Examining real-world examples of Redd.it malware provides valuable insights into its operation and impact. Below are two notable cases that highlight the importance of cybersecurity measures:
Case Study 1: Large-Scale Data Breach
In 2021, a Redd.it malware campaign resulted in a significant data breach affecting thousands of users. Attackers exploited vulnerabilities in outdated software, emphasizing the critical need for regular updates and proactive security measures.
Case Study 2: Targeted Phishing Attack
A targeted phishing attack using Redd.it malware compromised several corporate accounts, causing substantial financial and reputational damage. This incident highlighted the importance of employee training and robust security protocols in preventing and mitigating cyber threats.
Expert Recommendations for Enhanced Security
Cybersecurity experts recommend the following practices to enhance protection against Redd.it malware:
- Implement multi-factor authentication for all accounts to add an extra layer of security.
- Regularly back up important data to prevent loss in the event of an attack or system failure.
- Stay informed about emerging threats and prevention strategies to stay ahead of potential risks.
By following expert advice, you can fortify your defenses and minimize the risk of Redd.it malware infiltration, ensuring a more secure digital environment.
Creating a Secure Digital Environment
Building a secure digital environment requires a combination of technology, education, and vigilance. By adopting a proactive approach, you can ensure long-term protection against Redd.it malware and other cyber threats, fostering confidence and safety in your online activities.
Final Thoughts
Redd.it malware presents a significant challenge to digital security, but with the right knowledge and tools, you can effectively protect your system. By understanding its nature, recognizing signs of infection, and implementing prevention strategies, you can significantly reduce the risk of falling victim to this malicious software.
We encourage you to share this article with others and explore additional resources on our website. Together, we can promote a safer online community. Stay informed, stay vigilant, and stay secure!

![[100+] Malware Wallpapers](https://wallpapers.com/images/hd/malware-rrapbq5y7nqohg39.jpg)